Why Atlassian Guard (Atlassian Access) is a MUST for Secure Team Collaboration
Most JSM admins think SSO integration is “nice to have.” They’re wrong.
I recently had a client with 120 employees who spent weeks trying to figure out why their Azure AD integration wasn’t working the way they wanted. They had remote workers in Poland who couldn’t use the main SSO policy, agents who needed special API access, and internal users who were tired of constant password prompts when accessing the JSM portal.
The solution? Atlassian Guard (formerly Atlassian Access).
Here’s what most people don’t understand: if you’re running more than 50 users and want proper SSO integration with Azure AD, Google Workspace, or Okta, you can’t do it effectively without Guard. Sure, basic integration might be possible, but you won’t have the control you actually need.
Guard isn’t just about single sign-on, though the SAML integration alone makes it worth it. It’s about having granular policy control, excluding specific users from company-wide policies, managing API token access, and getting the security insights that help you sleep better at night.
The real game-changer? Your JSM portal users can access everything through SSO without needing to see a login screen. Browser detects their Windows credentials, passes them through Azure AD automatically, and they’re in. No passwords, no hassle, no security gaps.
At $4 per user (with volume discounts), it’s not free—but for any organization serious about security and user experience, it’s essential.
What is Atlassian Access?
Atlassian Access, often referred to as Atlassian Guard, plays a critical role in the security governance of your Atlassian Cloud products. It is particularly valuable for larger organizations that seek to implement SSO solutions like Azure Active Directory or Google Workspace. The importance of this tool cannot be overstated, as it allows companies to manage user access efficiently and securely.
Key Features of Atlassian Access
- Single Sign-On (SSO): This feature simplifies the login process for users, reducing the need for multiple passwords.
- Two-Factor Authentication (2FA): Adds an extra layer of security by requiring a second form of verification.
- Insights and Reporting: Provides administrators with visibility into user activities and access.
- Policy Management: Allows for the creation of specific access policies tailored to different user groups.
With these features, Atlassian Access not only enhances security but also improves user experience, making it a must-have for teams that prioritize collaboration and data protection.
The Importance of SSO Integration
One of the main reasons organizations are turning to Atlassian Access is for its seamless SSO integration. Imagine a scenario where your team can access all their tools with just one set of credentials. This not only streamlines the login process but also reduces the risk of password fatigue, where users might resort to unsafe practices like writing down passwords or using the same password across multiple platforms.
For instance, if your organization is using Azure Active Directory, integrating it with Atlassian Access provides a simplified login experience. Similarly, Google Workspace users can enjoy a hassle-free access process, as credentials are automatically passed when accessing Jira or Confluence.
Real-Life Examples of Atlassian Access in Action
To illustrate the value of Atlassian Access, let’s look at a couple of real-life examples that highlight its effectiveness.
Case Study 1: The Medium-Sized Company
Consider a medium-sized company in the UK with approximately 120 employees. Six to eight of these employees work remotely from Poland and do not have access to Azure AD. Without Atlassian Access, these remote workers would struggle with local access to Atlassian products, leading to potential security risks. However, with Atlassian Access, the company can easily manage access policies, allowing these remote workers to connect securely.
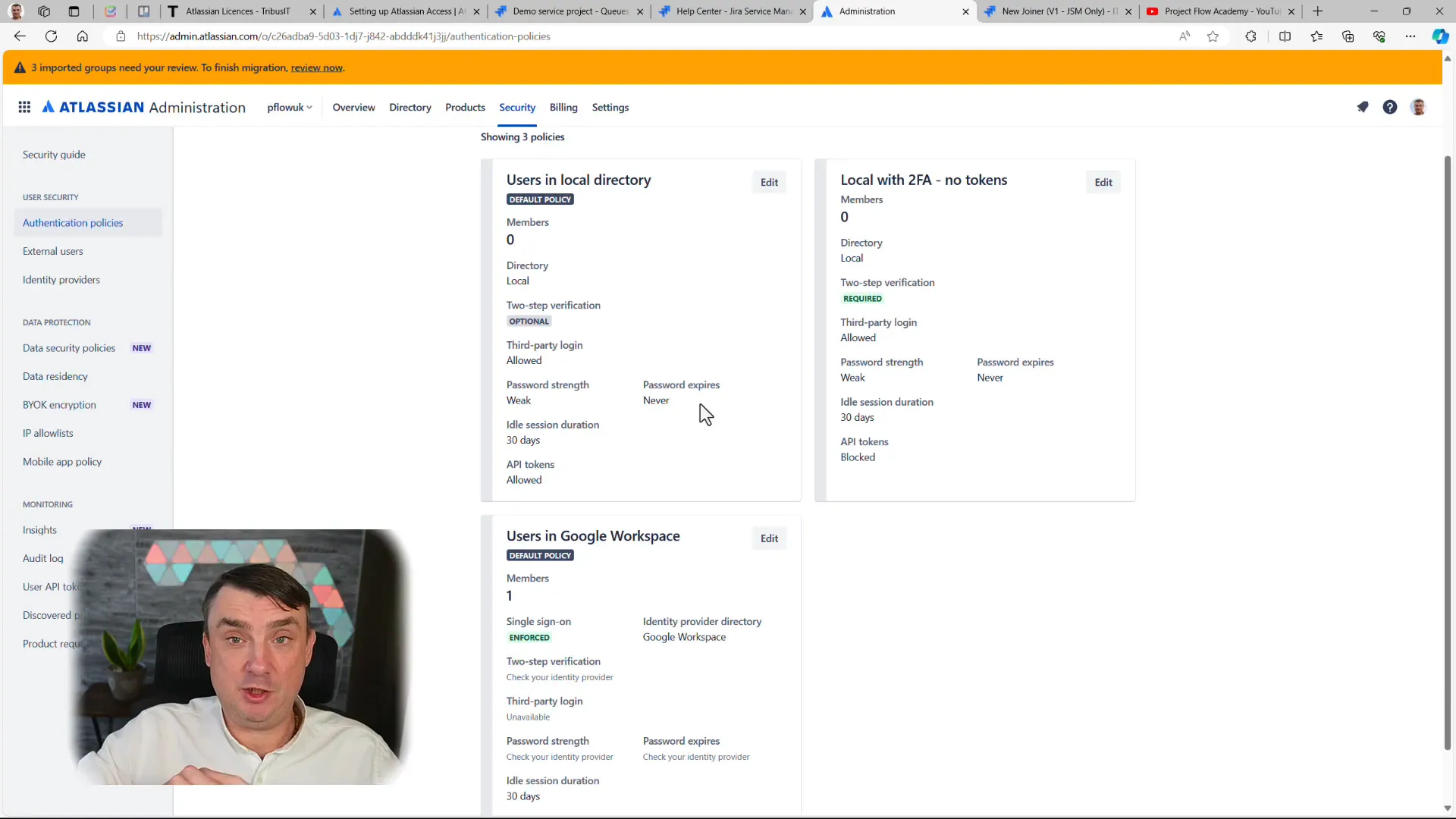
Case Study 2: Enhanced Security Features
Another client, a tech firm, integrated Atlassian Access to manage who can access sensitive tokens. By leveraging the policy management feature, the organization restricted token access to only two individuals, enhancing security while maintaining flexibility. This means that if a team member leaves or changes roles, the organization can quickly revoke access without disrupting workflows.
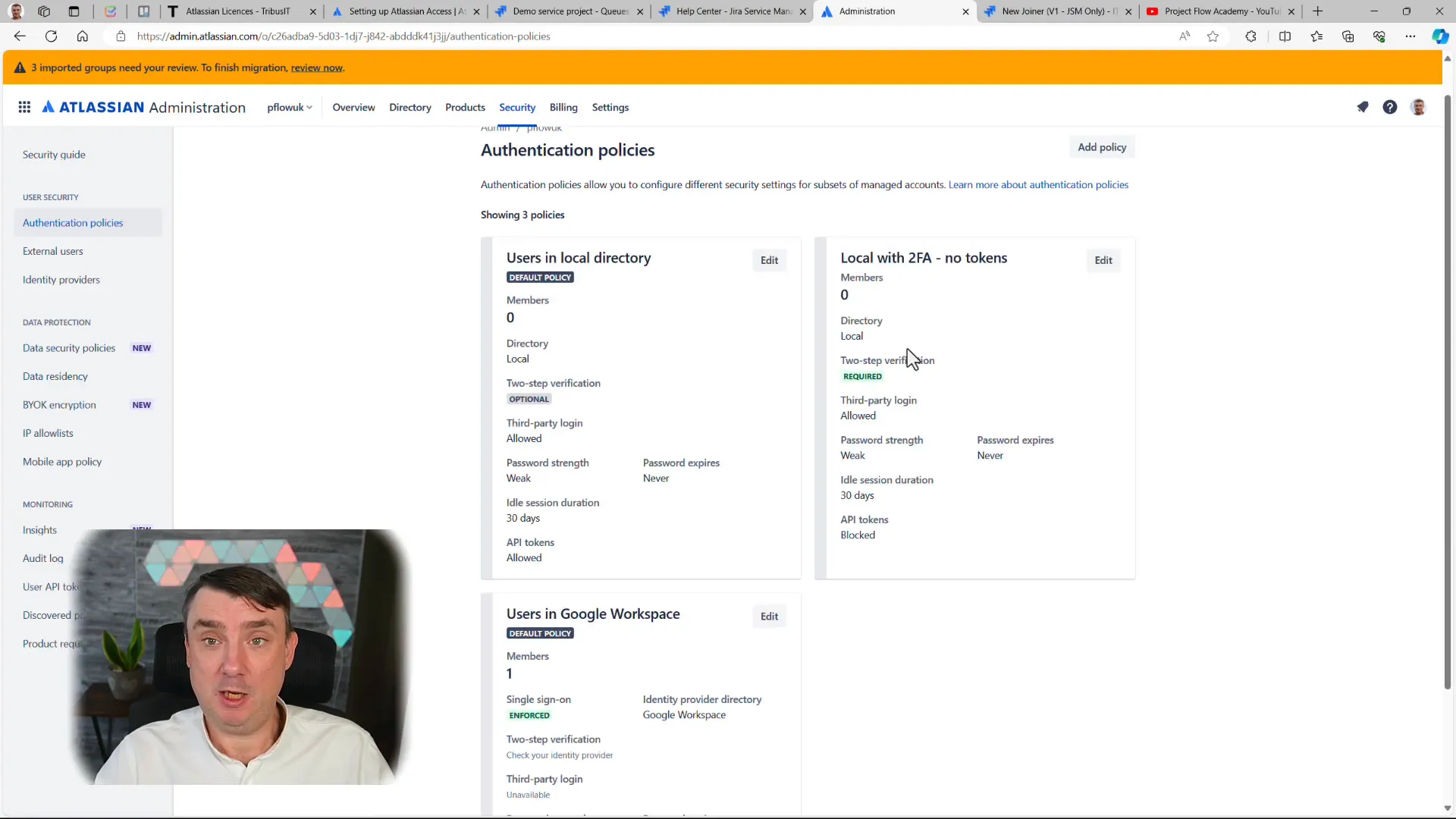
Insights and Reporting for Improved Security
Atlassian Access also provides valuable insights into user activities. Administrators can track who is using tokens and monitor access patterns. This data is crucial for identifying potential security threats or compliance issues, allowing organizations to take proactive measures to safeguard their data.
Pricing and Recommendations
While Atlassian Access is not a free product, the investment is worthwhile for organizations seeking enhanced security. Pricing typically starts around $254 per month, depending on the number of users. It’s advisable to reach out to a trusted partner like Tribus IT for a quote tailored to your organization’s needs.
When considering whether to implement Atlassian Access, think about the size of your organization and the complexity of your security needs. For teams utilizing Azure AD or Google Workspace, this tool is often a necessity.
Streamlining Jira Service Management (JSM)
Atlassian Access also significantly enhances Jira Service Management (JSM) capabilities. In many cases, organizations use JSM to provide internal users with access to support portals. Imagine having 120 users accessing the portal without needing to enter usernames or passwords. This is made possible through SSO integration, allowing credentials to be automatically passed and improving the user experience.
Enhancing Security and User Experience
The integration of SSO not only simplifies the login process but also enhances security by reducing the number of passwords that users need to remember. This is particularly important in today’s digital landscape, where data breaches are increasingly common.
Conclusion
In summary, Atlassian Access is more than just a product; it’s a vital tool for organizations looking to enhance security while improving collaboration. By enabling SSO, providing insights, and offering policy management, Atlassian Access empowers teams to work more effectively and securely.
If you’re considering implementing Atlassian Access, reach out to Tribus IT for assistance with licensing and consultation. Your organization deserves the best in security and efficiency, and Atlassian Access is a step in the right direction.
For more resources on Jira and Atlassian products, check out the free templates and guides available at this link.
Have thoughts or questions about Atlassian Access? Feel free to leave your comments below or reach out for personalised advice. Together, let’s unlock the full potential of your team with Atlassian Access!